|
|
|
| |
Information Security Management Practice (ISMP)
|
|
| |
ISO 27001 Consulting
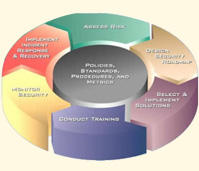
Information Security Policy:
The primary objective of this broad control area is to provide management with direction and support for information security in accordance with business requirements and relevant laws and regulations. Recommended processes include –
|
|
|
-
Setting out the organization’s policy for the protection of confidentiality, integrity and availability of its information assets, viz., hardware, software and information handled by information systems, networks and applications.
-
Establish the responsibilities for information security
-
Provide reference to documentation, which comprises the complete ISMS.
|
| Organization of Information Security
The primary control requirement is that a management framework be established to initiate and control the implementation of information security within the organization. Suitable management forum with appropriate leadership should be established to approve the information security policy, assign security roles and co-ordinate the implementation of security across the organization.
If necessary, a source of specialist information security advice should be established and made available within the organization. Contacts with external security specialists should be developed to keep up with industrial trends, monitor standards and assessment methods and provide suitable liaison points
|
|
 |
when dealing with security incidents. A multi-disciplinary approach to information security should be encouraged, eg. involving the co-operation and collaboration of managers, users, administrators, application designers, auditors and security staff, and specialist skills in areas such as risk management. |
Asset Management
The control requirement is that all major information assets should be accounted for and has a nominated owner. Accountability for assets helps to ensure that appropriate protection is maintained. Owners should be identified for all major assets and the responsibility for the maintenance of appropriate controls should be assigned. Responsibility for implementing controls may be delegated. Accountability should remain with the nominated owner of the asset.
Human Resource Security
The requirement under this key control area includes attaching significant importance to the HR security aspects of ISMS. Controls should ensure that security responsibilities be addressed at the recruitment stage, included in contracts, and monitored during an individual’s employment. Potential recruits should be adequately screened, especially for sensitive jobs. All employees and third party users of information processing facilities should sign a confidentiality and non-disclosure agreement. |
Physical and Environmental Security
The primary goal of this control measure is to prevent unauthorized access, damage and interference to business premises and information. This requirement is expected to be achieved by ensuring that critical or sensitive business information processing facilities be housed in secure areas, protected by a defined security perimeter, with appropriate security barriers and entry controls. They should be physically protected from unauthorized access, damage and interference. The protection provided should be commensurate with the identified risks.
|
|
 |
A clear desk and clear screen policy is recommended to reduce the risk of unauthorized access or damage to papers, media and information processing facilities.
Communications and Operations Management
Given that the primary goal of this branch of ISMS is to ensure the correct and secure operation of information processing facilities, various technical controls are discussed in this segment of ISMS. Responsibilities and procedures for the management and operation of all information processing facilities are required to be established. This includes the development of appropriate operating instructions and incident response procedures. Segregation of duties is recommended for implementation, where appropriate, to reduce the risk of negligent or deliberate system misuse. |
Access Controls
Within the broad objective of wanting to control access to business information, this covers policies and practices for information dissemination and authorization.
This covers both technical and organizational controls governing access to business assets at the user level, network level, in mobile computing and data in storage and in transit.
Information System Acquisition, Development and Maintenance
This will include infrastructure, business applications and user-developed applications. The design and implementation of the business process supporting the application or service can be crucial for security. Security requirements should be identified and agreed prior to the acquisition or development of information systems. |
|
 |
| All security requirements, including the need for fallbackarrangements, should be identified arrangements, should be identified at the requirements phase of a project and justified, agreed and documented as part of the overall business case for an information system. |
Information Security Incident Management
The primary purpose of the set of controls in this domain is to ensure that information security events and weaknesses associated with information systems are communicated in a manner allowing timely corrective action to be taken. It also requires that appropriate controls be put in place to ensure that a consistent and effective approach be applied to the management of information security incidents
Business Continuity Management
The primary goal is counteracting interruptions to business activities and to protect critical business processes from the effects of major failures or disasters. To achieve this, businesses must establish a business continuity management process.
This should be implemented to reduce the disruption caused by disasters and security failures (which may be the result of, for example, natural disasters, accidents, equipment failures, and deliberate actions) to an acceptable level through a combination of preventative and recovery controls.
Compliance
The principal goal of controls in this area is to avoid breaches of any criminal and civil law, statutory, regulatory or contractual obligations and of any security requirements. |
|
ISO27001 Preparedness Audit and Compliance Assessment
As customers seek greater assurance that they are dealing with a secure organization, they are seeking the assurance against globally relevant benchmarks. ISO-27001 defined ISMS can be regarded as a benchmarking for security policies, practices and procedures in the organization. While the accredited certification body provides the certification of compliance with the standard, the pre-certification task is detailed and time consuming.
After the gap analysis results indicate what needs to be done further to move towards creating a fully compliant ISMS, V-Tech consultants will work with client security personnel on creating the appropriate ISMS covering all the ten broad areas of security and controls addressed in ISO-27001. The service goes all the way till the accreditation auditor who can certify the client for compliance with the standard meets the client. |
|
 |
|
|
| |
|
|
|
 |

